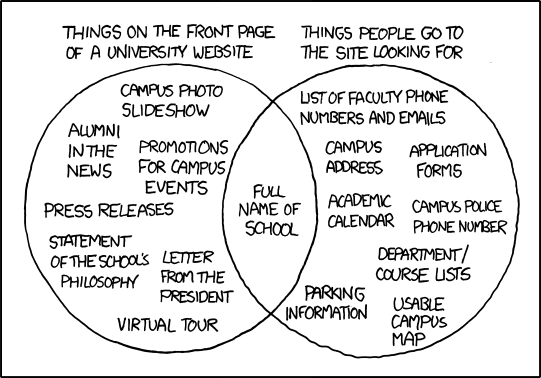
| University |
Things they tend to have |
Score |
Things people are looking for |
Score |
| Auckland University of Technology |
Yes: Full Name of school, Alumni in the news, Promotions for Compus events, Statement of School’s Philosophy,
No: Press releases, Letter from the president, Virtual tour |
5/8 |
Yes: Full Name of School, List of Facility phone number and Emails, Usable campus map, Campus Address, Application forms, Campus police phone number, Dept/Course lists, Parking information
No: Academic Calendar |
8/9 |
| Lincoln University |
Yes: Alumni in the news, Promotions for Campus events, Press Releases, Statement of School’s Philosophy, Full name of school
No: Campus photo slide-show, Letter from the president, Virtual tour |
5/8 |
Yes: Full name of school, List of Facility phone number and Emails, Campus Address, Application forms, Academic Calendar, Dept/Course lists, Parking information, Usable campus map
No: Campus police phone number |
8/9 |
| Massey University |
Yes: Full name of school, Alumni in the news, Promotions for Campus events, Press Releases, Statement of School’s Philosophy, Letter from the president
No: Campus photo slide-show, Virtual tour |
6/8 |
Yes: Full name of school, Campus Address, Application forms, Academic Calendar, Campus police phone number, Parking information, Usable campus map
No: List of Facility phone number and Emails |
8/9 |
| University of Auckland |
Yes: Full name of school, Alumni in the news, Promotions for Campus events, Press Releases, Statement of School’s Philosophy, Letter from the president
No: Campus photo slide-show, Virtual tour |
6/8 |
Yes: Full name of school, Academic Calendar, Campus police phone number, Dept/Course lists, Parking information, usable campus map
No: List of Facility phone number and Emails, Campus Address, Application forms |
6/9 |
| University of Canterbury |
Yes: Full name of school, Alumni in the news, Promotions for Campus events, Press Releases, Statement of School’s Philosophy
No: Campus photo slide-show, Letter from the president, Virtual tour |
5/8 |
Yes: Full name of school, List of Facility phone number and Emails, Campus Address, Campus police phone number, Parking information, Usable campus map, Dept/Course lists, Academic Calendar
No: Application forms |
8/9 |
| University of Otago |
Yes: Full name of school, Alumni in the news, Promotions for Campus events, Press Releases, Letter from the president, Statement of School’s Philosophy
No: Campus photo slide-show. Virtual tour |
6/8 |
Yes: Full name of school, List of Facility phone number and Emails, Campus Address, Application forms, Campus police phone number, Dept/Course lists, Parking information, Usable campus map
No: Academic Calendar |
8/9 |
| University of Waikato |
Yes: Full name of school, Campus photo slide-show, Promotions for Campus events, Press Releases, Statement of School’s Philosophy, Letter from the president
No: Alumni in the news, Virtual tour |
6/8 |
Yes: Full name of school, List of Facility phone number and Emails, Campus Address, Application forms, Academic Calendar, Academic Calendar,
Campus police phone number, Dept/Course lists, Parking information, Usable campus map
No: |
9/9 |
| Victoria University of Wellington |
Yes: Full name of school, Campus photo slide-show, Alumni in the news, Press Releases, Promotions for Campus events, Letter from the president, Statement of School’s Philosophy
No: Virtual tour |
7/8 |
Yes: Full name of school, List of Facility phone number and Emails, Campus Address, Application forms, Academic Calendar, Dept/Course lists, Parking information, Usable campus map
No: Campus police phone number |
8/9 |