Preventing the IoT Dystopia with Copyleft- Bradley M. Kuhn

- The S in IoT stands for Security
- Many stories of people hacking into baby monitors and home cameras
- IoT Devices often phone home to manufactorers website in order that you can access then remotely. “I suppose there are Chinese hackers watching my Dogs all day, I hope they will call me if they need water etc”
- Open source people have historically worked to get around problems like this.
- 1992 – If you wanted Linux, you downloaded the software onto floppies and installed it yourself. And Often had to work hard to make it work.
- Today only a small percentage of laptops sold have Linux on it.
- But Linux is commonly installed on IoT devices – 90% odd
- But
- No [easy] way to reinstall it yourself
- Much worse than laptops
- GPL includes “The scripts used to control the compilation and install of the executable”
- “Freedom to Study” is not enough
- Linksys Wifi router
- OpenWRT Project
- Release forced from Linksys and Cisco
- “Source as received from Linksys from GPL enforcement”
- Is OpenWRT a Unicorn
- Few projects with serious alternative firmware project
- Still sold new after 20 years
- BusyBox Lawsuits
- Before IoT was even a term
- At least one model of Samsung TV -> samygo.tv
- “Baffles me as to why do the manufactorers want us to buy more hardware”
- Linux focuses to much on big corp users and ignores hobbyist users
- Kernel peopel only care about the .c files. Don’t care about the install scripts etc.
- People at top of Linux now got their start hacking on the devices in front of them.
- The next generation of developers will be those hackers not from IBM and other big companies
- You didn’t need anything but a computer and an internet connection to become and upstream developer in those days. This is becoming less true.
- If the only thing you can install Linux on is a rackmount server, a cloud server or maybe a laptop and none of the IoT devices around you then things don’t look good….
- Linux was successful because users could install it on their own devices
- Linux won’t remain the most important GPL program if users can’t install their modifications. Tinkering is what makes Free software great.
- Upstream matters of course, but downstream matters more.
- There may be 1000s of Linux developers
- Put 2 billion people have Linux on their phone – Which is locked down and they can’t reinstall
- We don’t need a revolution to liberate IoT devices
- because the words are already there in the GPL
- We just have to take up our rights
- What you can do.
- Request Linux sources on every device you own – Companies have figured out people almost never ask
- Try to build and install them. If you can’t ask a friend or ask Conservancy for help
- If it doesn’t build/install it is a GPL violation, report it Conservancy
- Step up as a leader of a project devices that matter to you.
- Why this will work
- The problem seems insurmountable now, only because we have been led astray
- First and absolutely necessary step towards privacy and scurity on those devices
- When the user controls the OS again, the balance of power can be restored
- Questions
- Best way to ask for source code? Try email, the manual should say.
- How to get the new code on the device? Needs some push onto industry
- What if writing requires expensive equipment? Fairly rare, many devices allow over-the-air upgrades, we should be able to go the same way.
- Is there a list of compliant devices? – Proposed in past. Want to go softly at first in many cases
- Am I exposed to liability if I modify and distribute code I receive? – Almost certainly note, contact Conservatory if you are threatened.
Web Security 2019 – James Bromberger

- History of browser
- No images
- Images
- Netscape with crappy ‘International Security”
- https takeup is growing
- Chrome is hitting 60-70%
- 82% of browser are “modern”, crossover of chrome users to new version is about 3 months.
- PCI
- Remove early TLS in mid 2018
- TLS 1.1 and higher allowed
- The legacy browser has gone in the real world
- Some envs still behind, but moving ahead
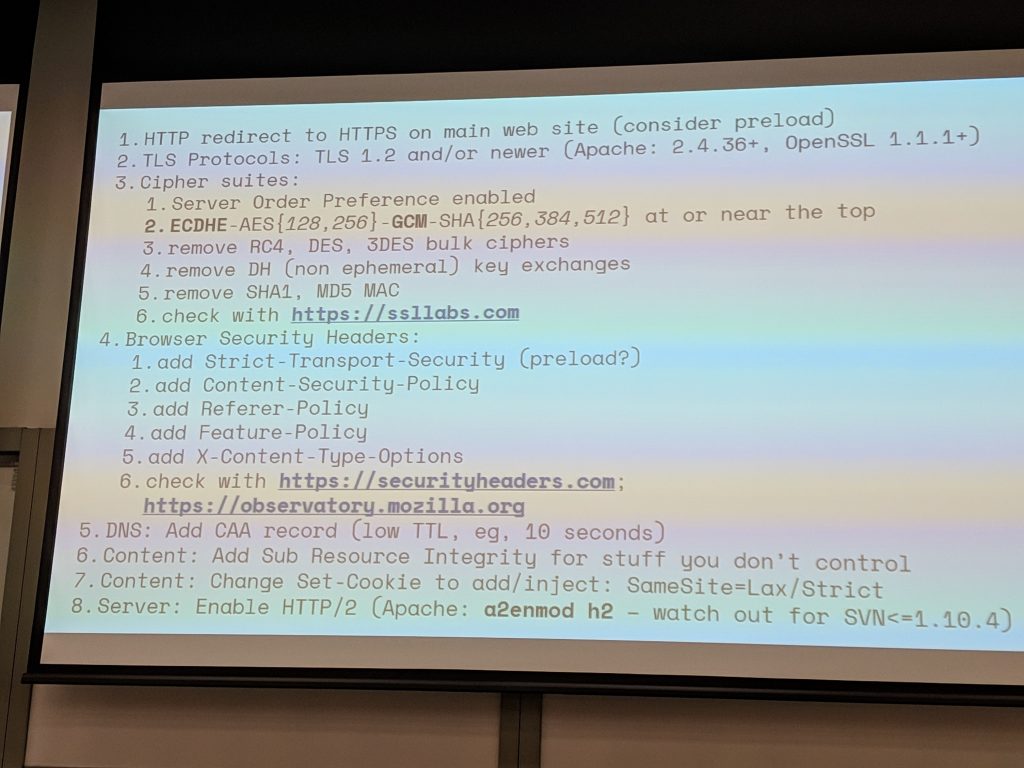
- What can we do with as little changes as possible?
- 0. Don’t use http, use https
- Use letsencrypt
- Stds reducing max length of certs from 5 years
- 1. TLS protocols
- 7 versions out there (old ones SSL).
- Most over 10+ years old
- Only 6 in the wild
- 3 not-known to be comprimised ( 1.1 1.2 1.3 )
- Very few clients only support 1.1 and not 1.2 (small gap in 2006-2008 ). IE supports 1.2. So maybe disable 1.1
- Log the protocol being used so you have data on your users
- OTOH not much supports 1.3 yet
- Use 1.2 and 1.3
- Turn off on the Browsers to
- Looks at which libraries you are using in code that makes https connections
- 2. Cypher Suite Optimisation
- New EC certs for key exchange
- New certs getting changed to ECDSA
- AES is standard for bulk encryption. GCM mode is best although windows 9 can’t do (Upgrade to 10!)
- MAC/Cehecksum – remove MD5, SHA1, remove SHA2-256+ , New ones coming
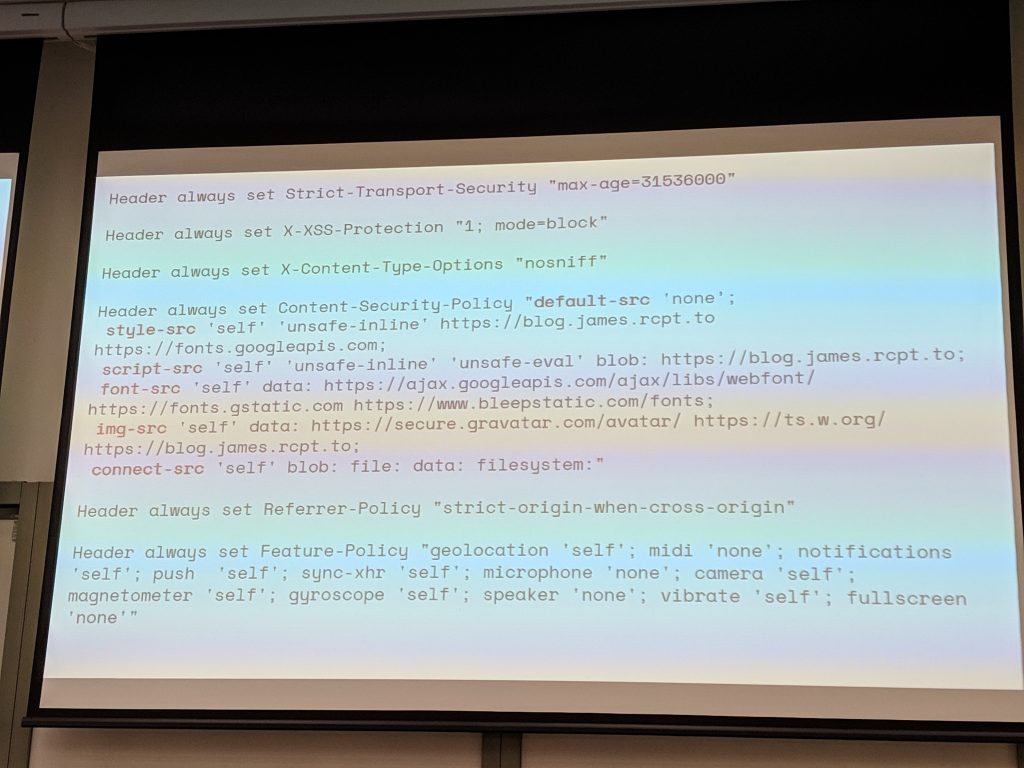
- Security Header
- Content-Security-Policy
- Referer-Policy – Usually locked down
- Feature-Policy – lots of stuff
- ” X-Content-Type-Options: no-sniff ” – don’t guess content type
- 4. CAA
- Around 200 Cert Authorities
- Authorized record type (CAA record) lists what CAs are allowed to issue certs for you.
- DNS Sec is useful – But during US Govt shutdown DNS keys are expring
- 5. Sub Resource Integrity
- Scripts included by html
- Can include checksums in html calling to varify
- 6. Cookies
- Secure – httpsonly
- “SameSite=Strict” – Reduces cross site request forgery
- 7. Http2
- Binary wire protocol
- Apache 2.4 on debian
- Forces better protocols
- 8. Lots more
- New compression algorithms
- Network error logs