With the cancelling of the SkyPath and the short-lived $800 million Pedestrian/Cycling bridge proposal it seems that the only options for the next harbour crossing will be a full scale tunnel or bridge.
However I came across the Youtube video where the author suggests a gondola crossing of Auckland Harbour. I did a bit of investigation myself and looked at some possible routes, the majority of which appear not to work but two might benefit from further investigation.
In the last decade urban gondola systems have become increasingly popular. They work well in difficult terrain such as steep hills, valley or river crossings. They are also relatively cheap which makes them popular in middle-income countries in the Americas.
The Medellin MetroCable in Columbia currently has 6 lines, most of these act as feeders from hill suburbs to Tram or Metro lines.
The Cablebús in Mexico City opened two lines in 2021 connecting low income transport-poor suburbs with metro stations.

Technology
The technology I am assuming is a Detachable Monocable Gondola with cars similar to the Emirates Air-Line in London, Medellin MetroCable and Mexican Cablebús.

Monocable means that there is a single moving cable. Detachable means that each car unhooks from the cable inside stations and moves slowly (or even stops) for easy boarding and unboarding. The general characteristics of these systems are:
- 8-10 person cars ( able to carry bicycles, wheelchairs etc )
- Speed around 20 km/h
- Capacity 2500 people/hour in each direction.
- Approx 1 car every 15 seconds.
Note that it is possible to increase capacity, for instance the new Medellin line P has a capacity of 4,000 people per hour in each direction.

Options for routes
I have provided details about two possible routes:
- Route One is a simple crossing of Auckland Harbour just east of the Auckland Harbour Bridge.
- Route Two connects the CBD (near Elliot Street), the University of Auckland and Parnell.
Note that apart from at stations cable systems are along able to make very slight turns at each tower. I have pretty much assumed each line will be straight apart of at stations.
Route One – East of the Bridge.
The will start from a station near the current Ponsonby Cruising Club. A 50m mast 150m north, then a 700m span across the harbour to another 50m mast and then a station in the Stokes Point Reserve.
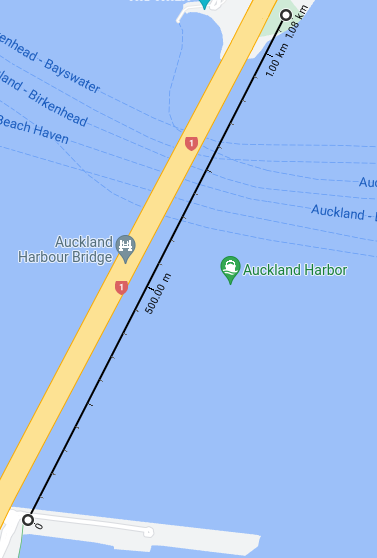
Total length is 1100m. Travel time around 5 minutes.
This route is a direct replacement of the Skypath. It would cater to cyclists and pedestrians needing to get between Stokes Point and Westhaven. The exact placement of the stations is flexible. The main difficulties are the height required to provide room for tall ships to pass underneath. The Emirates line has similar requirements to allow Thames river traffic and higher than usual towers.
Apart from some sightseers this line would mainly serve cyclists wishing to go directly between North Shore and the city. This Greater Auckland article shows the 2020 Skypath business case was estimating 4500 daily users for the Skypath a few years after it was built.

Route Two – Elliot Street to Parnell via Wellesley Street and the University
This would start with a station near the corner of Elliot Street and Wellesley Street West (possibly in front of Bledisloe House). The line would go east above Wellesley Street and over the Art Gallery, Albert Park and parts of the University to a station at the University (perhaps at the corner of Grafton Road and Symonds Street). The line would then go across Grafton Gully to a station at Parnell Train Station and then up the hill to terminate on Parnell Road. The total length is around 1700 metres.

There are 4 stations on this route.
- Parnell Village (near 236 Parnell Road) is an employment & entertainment area.
- Parnell Train Station is near Parnell and the University but down a hill from both and across busy roads from the University. It is within walking distance of the Auckland Museum.
- The University is well served by Symonds Street buses but not by rail and is cut off from the CBD and Parnell.
- The Elliot Street endpoint would be just 50 metres from both the Aotea Train Station and a proposed Queen Street light rail station near the Civic.
The idea of this line is to cross the difficult terrain that separates Parnell, Parnell Station, the University and the CBD. There should be a lot of possible journeys between these four. It will expand the effective radius of Aotea Station, Parnell Station and a Civic light-rail station. It would also improve Parnell’s connectivity.

Travel times ( assuming 20km/h speed and 1 minute per station ) on the most likely journeys:
| Journey | Walking Distance | Walking time | Cable distance | Gondola time |
| Elliot St to University | 800m | 11 min | 600m | 4 min |
| Elliot St to Parnell | 2100m | 30 min | 1700m | 9 min |
| Parnell Station to Parnell | 400m | 6 min | 250m | 3 min |
| Parnell Station to University | 1400m | 20 min | 800m | 5 min |
This line has the potential to be very busy. All the stops on the route would benefit from the improved inter-connectivity.
Two extensions to the line are possible. At the Parnell end the line could be extended down to a station located in the valley around St Georges Bay Road to serve the businesses (and housing) located around there.
Another possible extension of the line would be directly along Wellesley St West from Elliot Street to Victoria Park. I am unsure if traffic to/from the Victoria Park area would justify this however.
Other Routes
I had problems finding other routes that were suitable for gondolas. I’ve included a route to Birkenhead as an example of one that does not appear to be competitive with the existing bus as an example.
The majority of possible routes had various combinations of long distances (which take too long at 20km/h), low density/population at station catchment, already being covered by existing links and lack of obvious demand.
Westhaven to Birkenhead via Northcote Point and Marine Terrace.
This starts on the western side of the Harbour Bridge near a small Park/Bungy HQ. It goes over the harbour alongside the Bridge and has a station near “The Wharf”. The Line would then go across Little Shoal Bay to Little Shoal Bay Reserve. There would be a turning point there to go north-west over the gully of the Le Roys Bush Reserve to a station on the side of Birkenhead Avenue near the viewing platform.
Length 3.9km and end to end travel time of around 15 minutes.
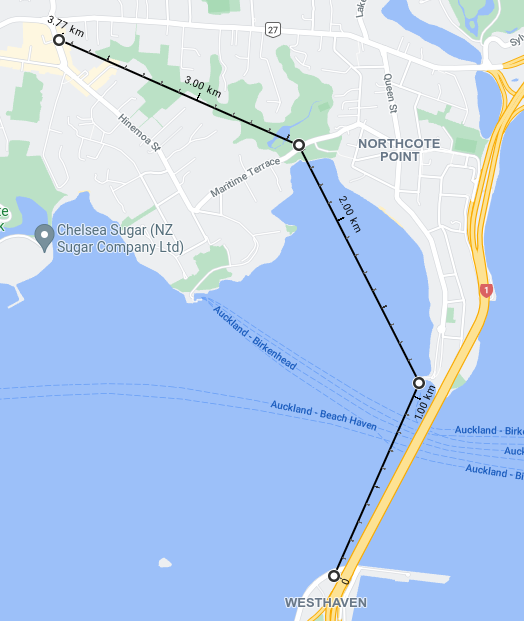
The problem with this line is that Westhaven is not a good destination. Route One across the harbour fills a gap for cyclists but extending the line to Birkenhead doesn’t seem significantly improve the catchment (especially for non-cyclists).
Other possible routes I looked at
- A simple crossing West of the Bridge
- From the south-east of St Mary’s Bay to Stokes Point
- From Wynyard Quarter to Stokes Point.
- From St Mary’s Bay to Stokes Point and then the Akoranga Bus station
- From Wellesley Street West to Stokes Point.
- Between Devonport and the city
- Above Lake Road from Devonport to Takapuna
- Between Stokes Point and Bayswater
- Between Akoranga Bus station and Devonport
Conclusion
Urban Gondolas do not work as a general solution to urban public transport but are suited to certain niche routes across difficult terrain.
Starting from the simple harbour crossing I looked at several cross harbour routes but most were unpromising due to lack of under-served destinations that could be easily connected. I ended up just keeping the basic harbour crossing to fill the gap for cyclists and walkers.
The Elliot Street to Parnell line on the other hand might be a good fit for a gondola. It is less than 2km long but connects 3 popular locations and an under-utilised train station.
Costs of gondolas are fairly low compared to other PT options. The two Cablebús lines in Mexico City are each around 10km long and cost $US 146m and $US 208m. Ballpark estimates might be between $NZ 100 million to $NZ 200 million for each route, hopefully closer to $100m.